To underscore the critical importance of robust M365 security, let's examine some high-profile incidents:
One of the most significant threats to M365 came from the Nobelium group, the same actors responsible for the SolarWinds supply chain attack. This sophisticated operation targeted the email accounts of Microsoft's senior executives. The attack highlighted the ability of advanced threat actors to penetrate even the most fortified digital defenses.
- Microsoft Cloud Email Breach
In a more recent example, a breach impacted U.S. government agencies, compromising email accounts of high-ranking officials. This incident underscored the vulnerability of cloud-based email systems and the potential for severe consequences when security measures are inadequate.
These cases serve as stark reminders that no organization is immune to cyberattacks. Even tech giants like Microsoft can be targeted, emphasizing the need for constant vigilance and proactive security measures.
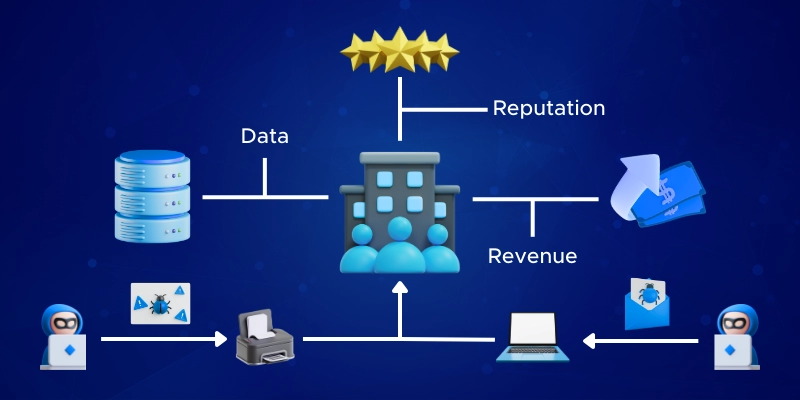
You might think, "Why would hackers target my small business? I don't have any valuable data." But this is a dangerous misconception. Cybercriminals often use compromised systems as steppingstones to attack larger targets. Your infrastructure could be unknowingly transformed into a botnet, a network of infected devices used to launch attacks on high-profile companies. This makes you a potential accomplice in cybercrime, exposing your business to significant legal and financial risks.